
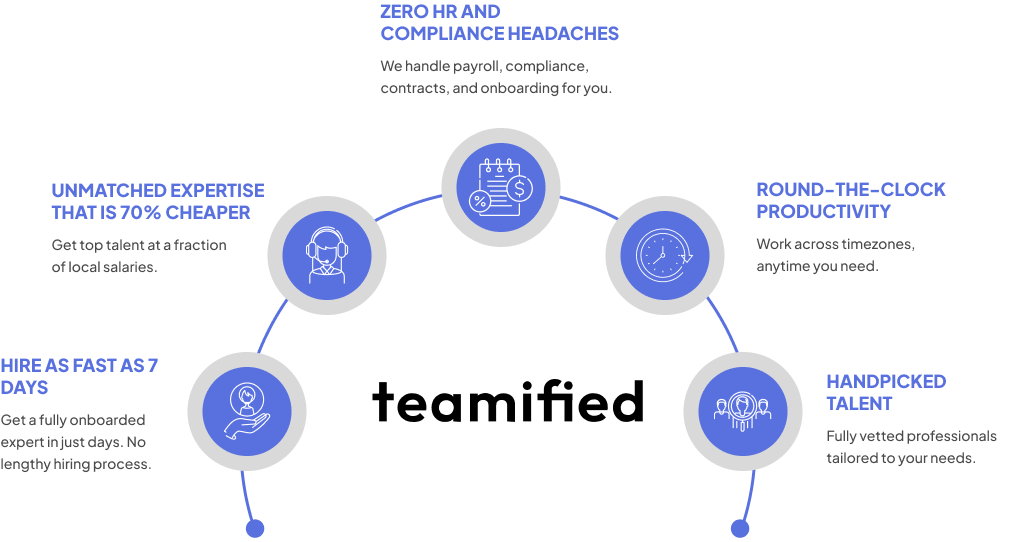





















.svg.avif)











.svg.avif)









.svg.avif)













.avif)
.avif)


.png)








.avif)


.avif)
.avif)
.avif)










.svg.avif)







.svg.avif)











.svg.avif)

































.svg)
.svg)






We’re proud to have a 4.6 Glassdoor rating that backs that up. Because when people love showing up, great things happen.












.svg)
.svg)
.svg)
.svg)
.svg)
.svg)










With Teamified’s streamlined hiring process, you can onboard a qualified NOC technician in half the time compared to traditional hiring methods.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
With Teamified’s streamlined hiring process, you can onboard a qualified NOC technician in half the time compared to traditional hiring methods.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
Yes. Data privacy and security protocols are a key part of our onboarding process.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
Absolutely. We prioritise data confidentiality and ensure secure handling of all financial information.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
Yes, provided you work with vetted professionals and clear IP protections. Teamified ensures secure collaboration with skilled developers from regions like India, Brazil, Philippines, and many more.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
Teamified’s hiring process enables you to bring on an SEM expert 50% faster than standard recruitment.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.
They follow strict security protocols and industry compliance standards, ensuring your network remains protected from vulnerabilities and potential cyber threats.